
Week4
This was the final week and we were given an Android dump.
We only had 9 questions and I wasn’t too sure how this one would pan out as I have never done forensics on Android devices before but I suspected it would be similar to any other device just the difference would be the operating system and where the files were located.
Once we downloaded the files and extracted them we were good to go.
1) Device Time
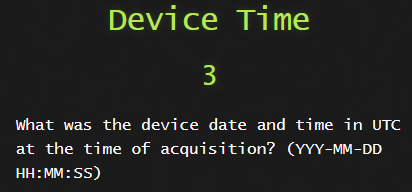
We can get the following in a file called device_datetime_utc.txt

2) Downloads
Let’s have a look for a tor browser program that was downloaded and it should have a file extension with an apk. apk is an Android package file that’s used to install an application.
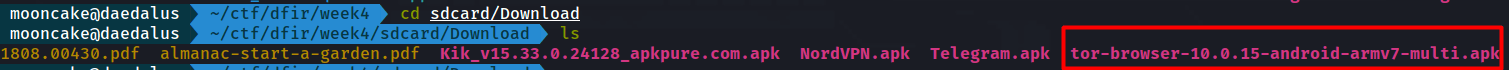
As we see there is the downloaded Tor Browser apk.
Now we need to see what time it was downloaded.
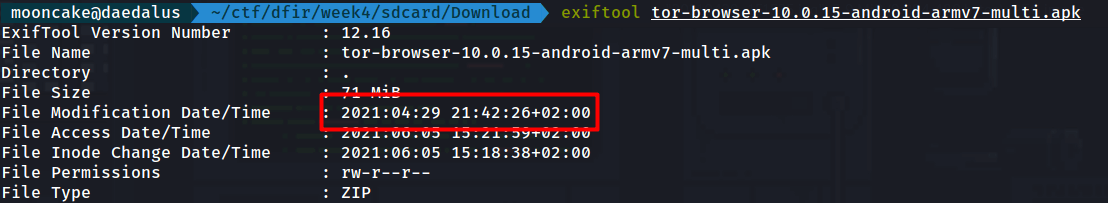
What we see here is not the time in UTC time.
You notice there is a +02:00 which means I am 2 hours ahead of UTC.
So the answer is asked for in UTC time so the answer would be 2021-04-29 19:42:26
3) Email
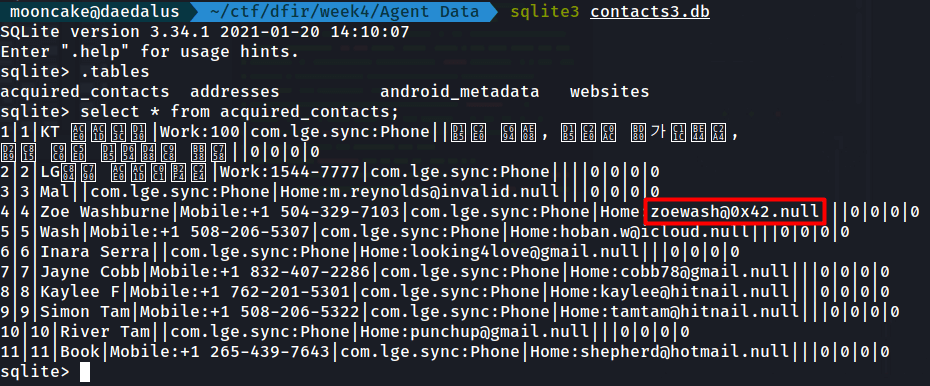
This one I found in the Agent Data folder.
There is a file contacts3.db.
The .db file is a sqlite database file.
So I opened it up in sqlite3 and found the email address.
4) App Focus
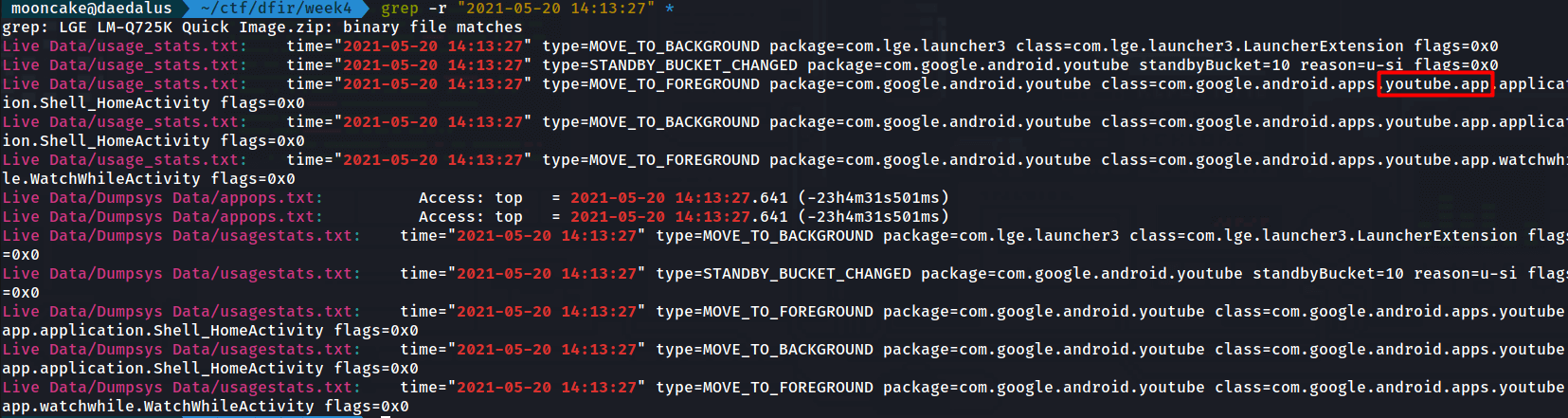
Solving this in unix felt like cheating but hey, you use the tools you have.
I used grepped for the exact time in the all the folders and found the app being used.
If you want to manually check, you can just check the usage_stats.txt file under Live Data and check the time to see what app is being used there.
5) Power!
Here we go to a file Live Data/Dumpsys Data/batterystats.txt
We see the time the device was reset.
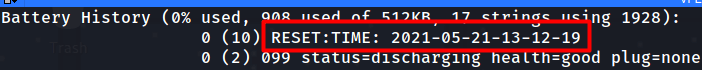
We now have to look for when the device charged to 100%.
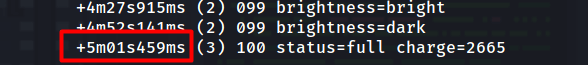
Now we need to calculate the time of when the device charged to 100%.
So we just need to take 13:12:19 and add 5 minutes, 1 second and 459 milli seconds to it but then round it off to the nearest second.
2021-05-21 13:17:20
6) WIFI
Using sqlite3 again, we look at the wifi.db in the Agent Data and we get a list of all the WiFi points the device has tried to connect to.
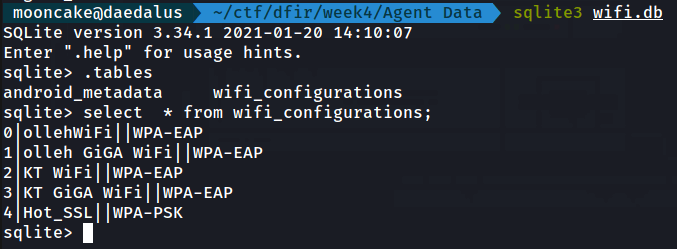
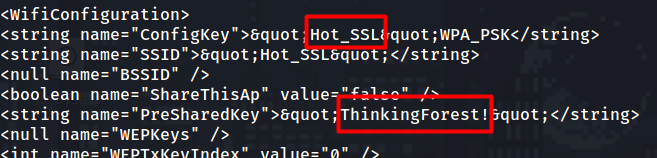
Seems like the last WIFI it connected to was Hot_SSL.
After grepping through the files for the Hot_SSL I come across the following file.
apps/com.android.providers.settings/k/com.android.providers.settings.data
In there we find the following
7) Always watching
We go back to the file usage_stats.txt and we grep for the date and the Youtube application.
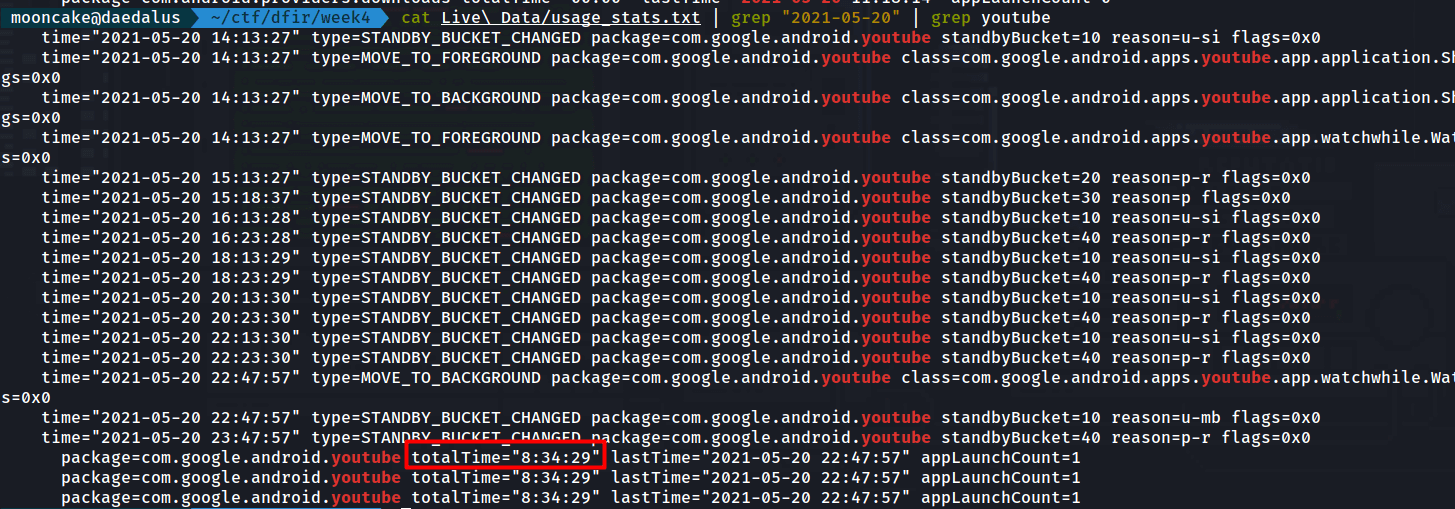
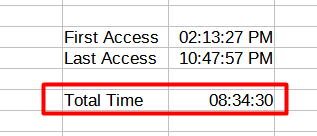
I entered 08:34:29 and it was wrong.
Wait what?
I then manually entered the first time Youtube was accessed until the last time.
8) Copied?
This challenge I remembered a strange file from week 1.
The only files that the user copied were the pictures from the camera and the pdf we found.
It was under
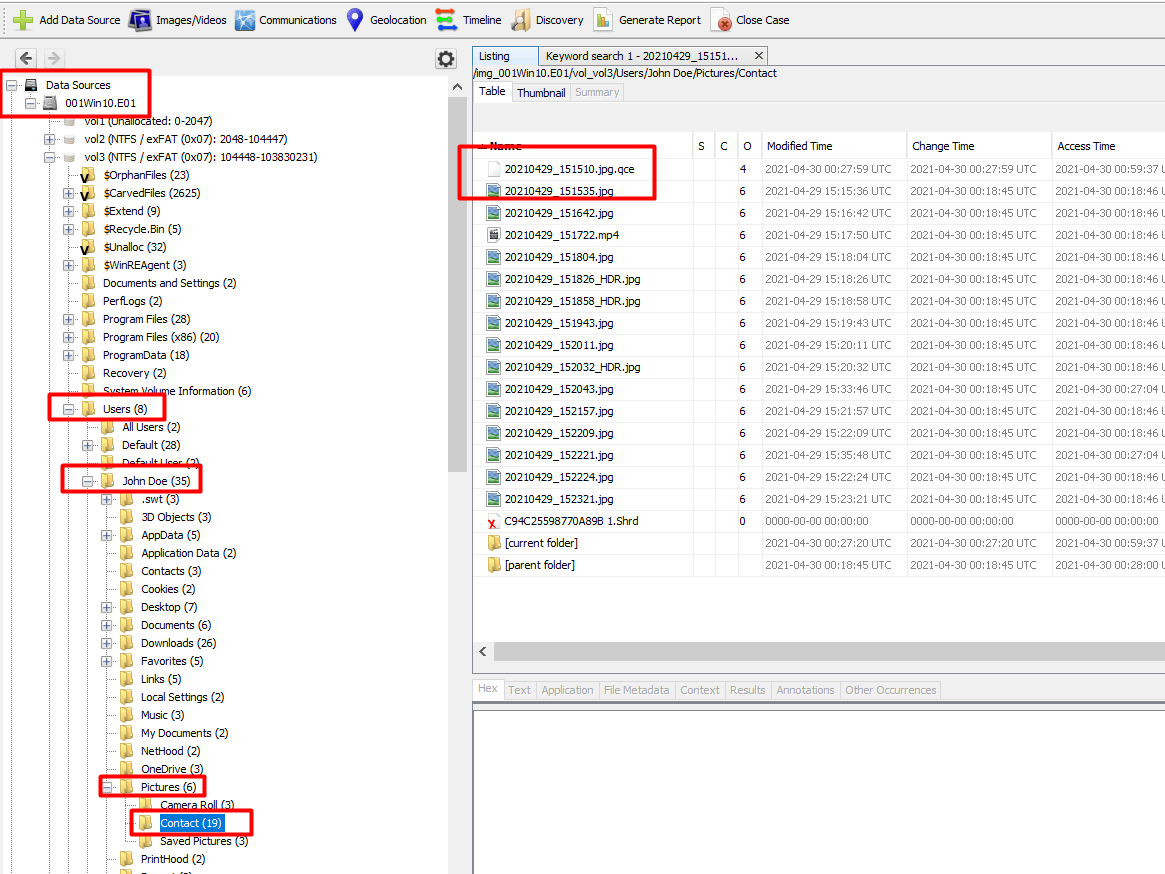
.qce is a QuickCrypto program which encrypts files.
I also remember QuickCrypto being installed on the system.
9) Structural Similarity
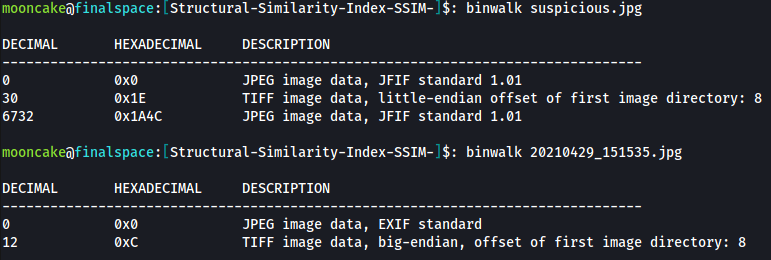
This one was pretty challenging. We had to download a certain image, I named it suspicious.jpg

We had to find the same image that was taken on the phone.
Easy.
We go to the sdcard/DCIM/Camera folder.
It’s called 20210429_151535.jpg
We put both the images in a directory.
When we do a binwalk we can clearly see something is up with the suspicious.jpg file
I did a google search for find the structurual similarity metric of jpg
I came across the following page
How to calculate the Structural Similarity Index (SSIM) between two images with Python
I followed the instructions
1
pip3 install scikit-image opencv-python imutils
and then copied the code on the site.
1
python3 script.py --first original_image.png --second compressed_image.png
After running the script I got an error.
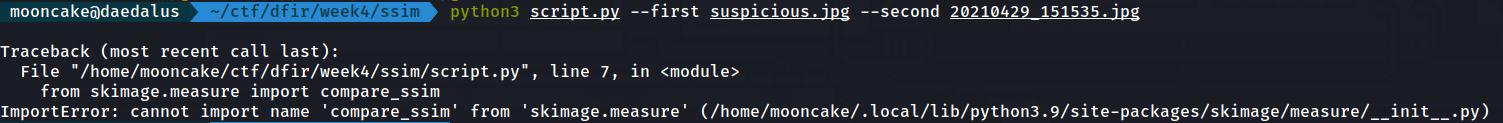
After some googling and research I found out that the code that the person posted, they were using the old method and the newer version of skimage uses a new method.
I changed the two following lines in the script.
1
2
#from skimage.measure import compare_ssim
from skimage.metrics import structural_similarity as ssim
1
2
#(score, diff) = compare_ssim(grayA, grayB, full=True)
(score, diff) = ssim(grayA, grayB, full=True)
Once we run the script again we get the SSIM.
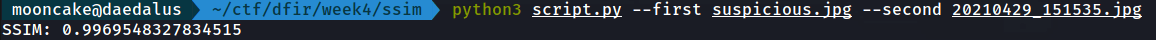
Conclusion
Android forensics went better than I thought. I thought we would have to use Android Studio or something like that but glad it was much simpler than that.
Thank you for reading these write ups. It was fun to redo them.
I am by no means a DFIR guru but this was a very fun CTF to do.